...
- Latency in data access (multiple serializations)
- Data transformation (multiple representations)
- Data duplication (multiple representation 'cached' in multiple data stores)
Option B
Common information model and data lake. (Another extreme)
...
Access control may be used to mitigate the negatives of this approach. However this can be problematic in the selection of the DB technology, and the load on the DBMS
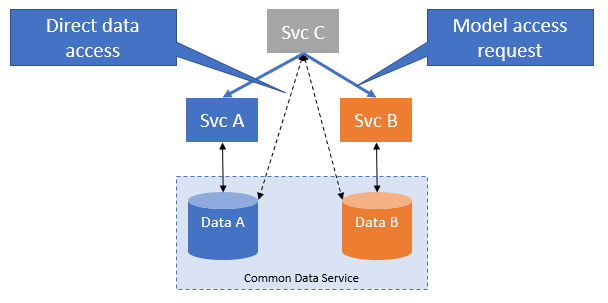
Option C
Hybrid approach.
...
Access control may be used to enhance the 'security-through-obscurity', without impacting complexity, DB technology selection or data access performance.
This approach is backwardly compatible with Option A.