| Project Name | Application Authorization Framework |
|---|---|
| Target Release Name | Beijing Release |
| Project Lifecycle State | Incubation |
| Participating Company | AT&T, Intel, Tech Mahindra |
AAF trying to address the secured communication threw certificate management & token based Authentication,Authorization
The existing Amsterdam use cases are still going to be supported and additional use cases related to the will be supported for the Beijing Release
For Beijing release, the minimum viable product we are targeting is integrating AAF with multiple ONAP applications and perform secured transactions.
List the functionalities that this release is committing to deliver by providing a link to JIRA Epics and Stories. In the JIRA Priority field, specify the priority (either High, Medium, Low). The priority will be used in case de-scoping is required. Don't assign High priority to all functionalities.

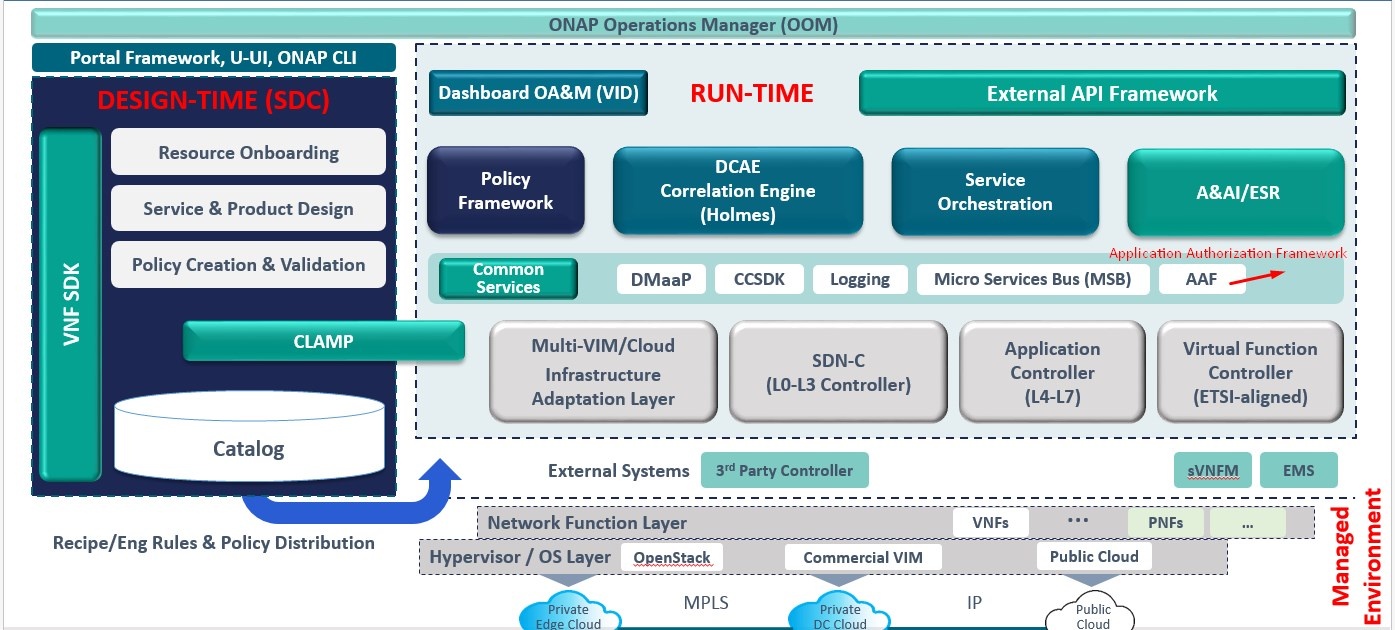
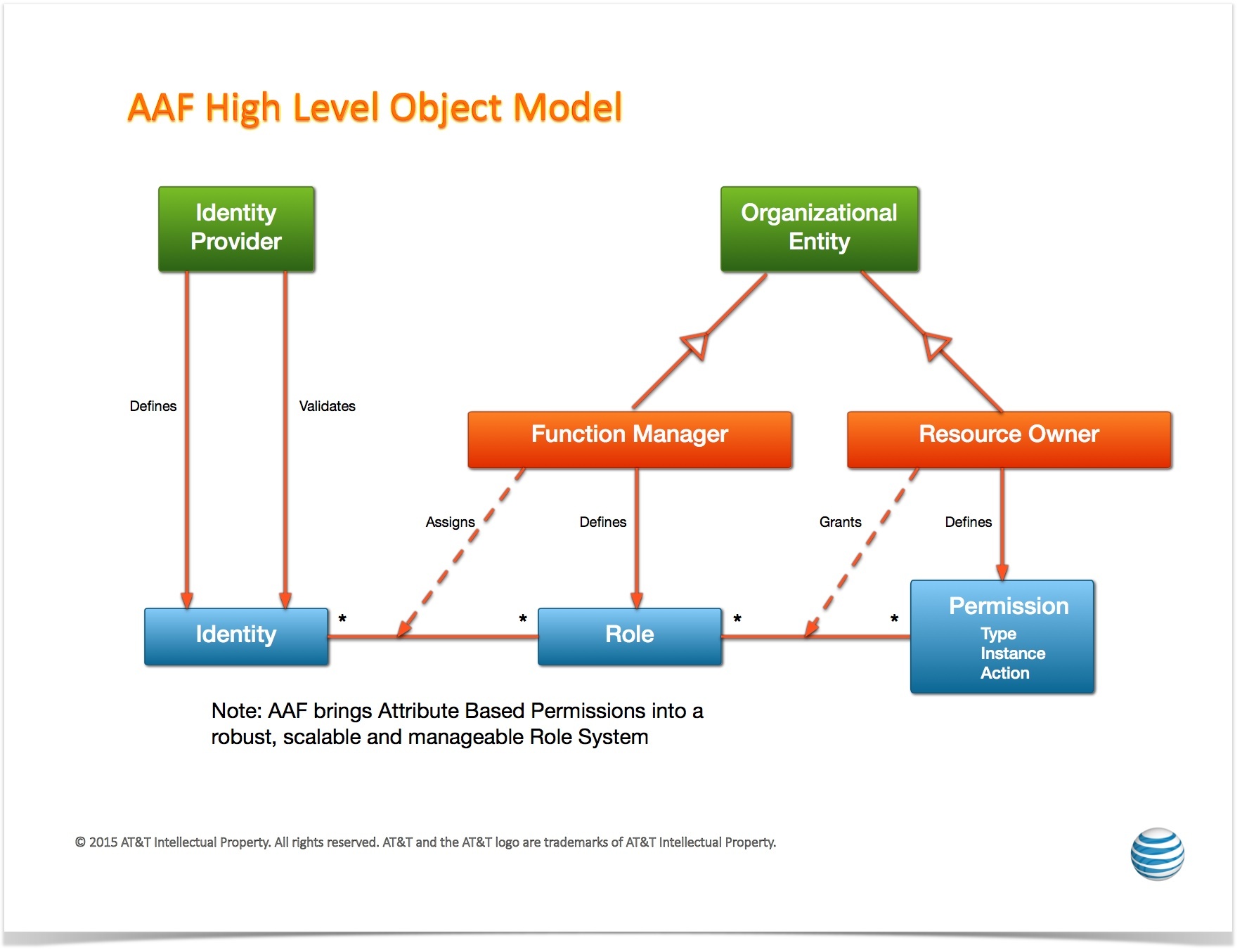
AAF is to organize software authorizations so that applications, tools and services can match the access needed to perform job functions. This is a critical function for Cloud environments, as Services need to be able to be installed and running in a very short time, and should not be encumbered with local configurations of Users, Permissions and Passwords.To be effective during a computer transaction, Security must not only be secure, but very fast. Given that each transaction must be checked and validated for Authorization and Authentication, it is critical that all elements on this path perform optimally.
Indicate the outcome (Executable, Source Code, Library, API description, Tool, Documentation, Release Note...) of this release.
Deliverable Name | Deliverable Description |
|---|---|
AAF integration with Appc | AAF Git repository |
| AAF source code | AAF Git repository |
| AAF library | ONAP Nexus repository |
| AAF API description | ONAP wiki |
| AAF Release Notes | ONAP wiki |
| AAF Documentation | AAF Git repository |
As part of the Beijing release,Certificate Management will be added to the AAF
Refering to CII Badging Security Program and Platform Maturity Requirements, fill out the table below by indicating the actual level , the targeted level for the current release and the evidences on how you plan to achieve the targeted level.
| Area | Actual Level | Targeted Level for current Release | How, Evidences | Comments |
|---|---|---|---|---|
| Performance | 0 | 1 | Run performance basic test, depends on performance criteria availability for level 1 |
|
| Stability | 0 | 1 | Participate to Stability runs Level 1 |
|
| Resiliency | 1 | 1 |
| |
| Security | 0 | 1 | Reach CII passing badge, increasing test coverage as remaining item |
|
| Scalability | 0 | 1 | Reach Level 1 single site horizontal scaling |
|
| Manageability | 1 | 1 | Using LOG4J common framework for logging |
|
| Usability | 1 | 1 | API documentation provided |
|
List the API this project is expecting from other projects.
Prior to Release Planning review, Team Leads must agreed on the date by which the API will be fully defined. The API Delivery date must not be later than the release API Freeze date.
Prior to the delivery date, it is a good practice to organize an API review with the API consumers.
API Name | API Description | API Definition Date | API Delivery date | API Definition link (i.e.swagger) |
|---|---|---|---|---|
| None | None | None | None | None |
API this project is delivering to other projects.
API Name | API Description | API Definition Date | API Delivery date | API Definition link (i.e.swagger) |
|---|---|---|---|---|
| Provisining | API for creating,deleting and listing the administrative objects | Aug 02 2017 | March 08 2018 | AAF API |
| Admin API | API for the admin access | Aug 02 2017 | March 08 2018 | AAF API |
| CADI | CADI ( CODE ACCESS DATA IDENTITY) | Aug 02 2017 | March 08 2018 | AAF API |
Third Party Products mean products that are mandatory to provide services for your components. Development of new functionality in third party product may or not be expected.
List the Third Party Products (OpenStack, ODL, RabbitMQ, ElasticSearch,Crystal Reports, ...).
Name | Description | Version |
|---|---|---|
| Docker | Container engine | 1.12 |
| Cassandra | database container | 2.1.16 |
In case there are specific dependencies (Centos 7 vs Ubuntu 16. Etc.) list them as well.
Provide a description of the testing activities (unit test, functional test, automation,...) that will be performed by the team within the scope of this release.
Describe the plan to integrate and test the release deliverables within the overall ONAP system.
Confirm that resources have been allocated to perform such activities.
AAF will invest in CSIT tests to allow further integration testing, AAF already provided some tests as part of R1.
This section is used to document a limitation on a functionality or platform support. We are currently aware of this limitation and it will be delivered in a future Release.
List identified release gaps (if any), and its impact.
Gaps identified | Impact |
|---|---|
| Testing/Integration | limited testing of final product |
Provide a link toward the list of all known project bugs.

Fill out the Resources Committed to the Release centralized page.
The milestones are defined at the Release Level and all the supporting project agreed to comply with these dates.
This section may be used to document internal milestones that the team agreed on.
Also, in the case the team has made agreement with other team to deliver some artifacts on a certain date that are not in the release milestone, provide these agreements and dates in this section.
It is not expected to have a detailed project plan.
Date | Project | Deliverable |
|---|---|---|
| To fill out | AAF | AAF - CertMan,oAuth |
http://onap.readthedocs.io/en/latest/submodules/aaf/authz.git/docs/index.html
The Documentation project will provide the Documentation Tool Chain to edit, configure, store and publish all Documentation asset. |
If this project is coming from an existing proprietary codebase, ensure that all proprietary trademarks, logos, product names, etc. have been removed. All ONAP deliverables must comply with this rule and be agnostic of any proprietary symbols.
FOSS activities are critical to the delivery of the whole ONAP initiative. The information may not be fully available at Release Planning, however to avoid late refactoring, it is critical to accomplish this task as early as possible.
List all third party Free and Open Source Software used within the release and provide License type (BSD, MIT, Apache, GNU GPL,... ).
In the case non Apache License are found inform immediately the TSC and the Release Manager and document your reasoning on why you believe we can use a non Apache version 2 license.
Each project must edit its project table available at Project FOSS.
Charter Compliance
The project team comply with the ONAP Charter.