The steps that were followed to generate certificates to be used to deploy the CMSO Spring Boot services in OOM with HTTPS enabled in Windriver Lab. This assumes you already have access to the Windriver Lab.
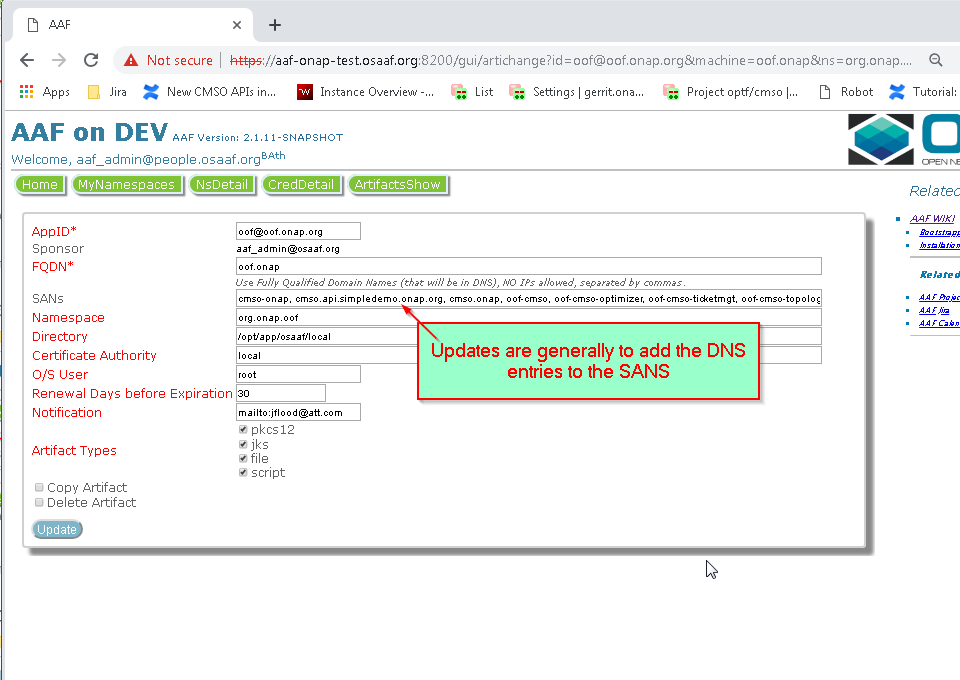
Updating the oof.onap Certificate in AAF
In order to access AAF https://aaf-onap-test.osaaf.org:8200/gui/home you will need to update your /etc/hosts file (C:\Windows\System32\drivers\etc\hosts on Windows)
| 10.12.5.145 aaf-onap-test.osaaf.org |
|---|
Note that the IP can change. Not sure how to find out where it is running when it does. Found it here https://docs.onap.org/en/latest/submodules/aaf/authz.git/docs/sections/configuration/AAF_4.1_config.html, but this could change too
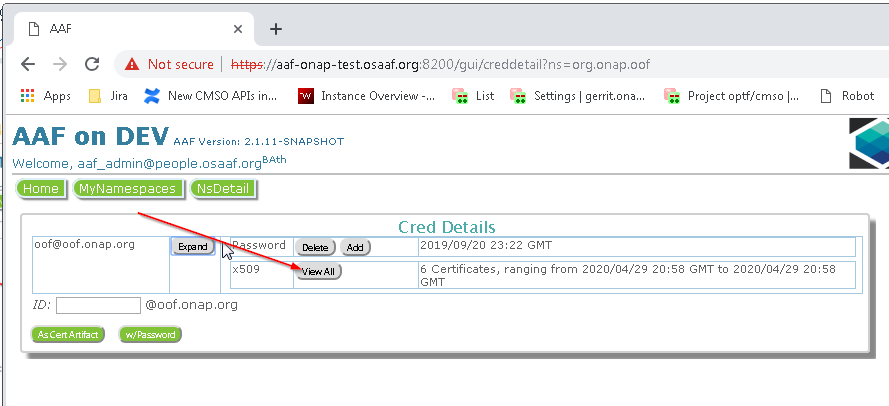
Navigating to the AAF Certificate
From here: https://aaf-onap-test.osaaf.org:8200/gui/nsdetail?ns=org.onap.oof
Or, if you want the oof.onap certificate, just click on https://aaf-onap-test.osaaf.org:8200/gui/artichange?id=oof@oof.onap.org&machine=oof.onap&ns=org.onap.oof
Downloading the AAF certificate Artifacts
This must be done from a host that can run docker and has it's etc hosts updated as above:
| 10.12.5.145 aaf-onap-test.osaaf.org |
|---|
This is the Reader's Digest version of https://docs.onap.org/en/latest/submodules/aaf/authz.git/docs/sections/configuration/AAF_4.1_config.html
- Download https://gerrit.onap.org/r/gitweb?p=aaf/authz.git;a=blob_plain;f=auth/docker/agent.sh;hb=HEAD
- Rename file to agent.sh
Running agent.sh will prompt for many arguments which will be stored in ./aaf.props file. Subsequent executions of agent.sh will pull the values from aaf.props so if you need to change a value, it should be done in aaf.props (or delete it and start over)
agent.sh will run a docker image which will download all the artifacts to the Directory /opt/app/osaaf/local in the docker image.
The Application FQDN is the FQDN * oof.onap so we will add our Windriver lab VPN IP that to our /etc/hosts file as well
| 10.12.5.145 aaf-onap-test.osaaf.org 10.12.25.177 oof.onap |
|---|
On Unix host, run ifconfig while connected to the VPN
| ifconfig -a|grep 10.12 inet 10.12.25.177 --> 10.12.25.178 netmask 0xffffffff |
|---|
These files will not be accessible by default when the script is done because it is going to a docker volume that is in the VOLUME attribute in aaf.props. For some reason, the script does not allow the VOLUME to be a local folder. The docker volume will automatically be created, in the case below docker volume cert (volume can be any name) created with the local driver.
WIth luck this will have generated all of the artifacts in the docker cert volume:
Retrieving the artifacts from the docker volume
Note that when we retrieve the artifacts, the various passwords will be encrypted and can only be unencrypted by cadi. The cadi showpass command expects the artifacts to be in /opt/app/osaaf/local folder, so the following command can be used to put the files from the cert docker volume into your local /opt/app/osaaf/local folder.
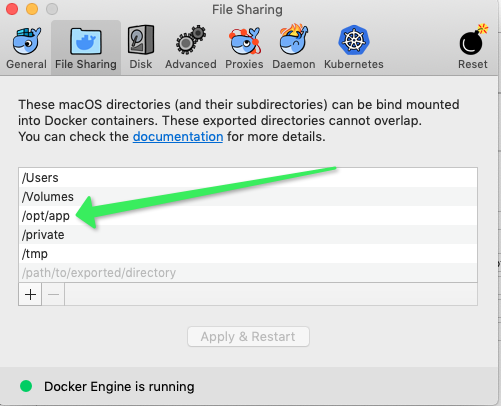
Important note on the Mac, had to update the docker preferences to include /opt/app as a mountable folder.
| sudo docker run -v /opt/app/osaaf:/tmp/osaaf -v cert:/opt/app/osaaf/local ubuntu cp -rf /opt/app/osaaf/local/local /tmp/osaaf |
|---|
In essence the above runs a docker container (ubuntu) with the docker cert volume mounted and the local /opt/app/osaaf/local folder mounted as a different volume so we can copy the artifacts from the docker volume to our local host.
Retrieving the artifact passwords
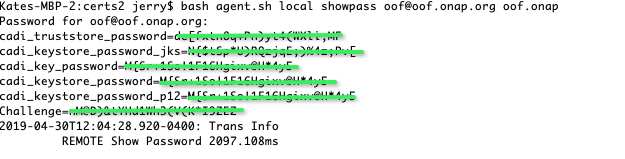
The agent.sh can be used to decrypt the passwords in the org.onap.oof.cred.props file.
There are several things to address.
- Copy the truststoreONAPall.jks to the agent.sh folder
- Make sure the CADI jar agent.sh is in the local folder. You will get this error: For local use, you need to have 'aaf-cadi-aaf-2.1.12-SNAPSHOT-full.jar'
- The AAF account you are using needs to have showpass privieges in AAF, so we added those privileges to the admin role in the namespace
For 1:
| cp /opt/app/osaaf/local/truststoreONAPall.jks ./ |
|---|
For 2:
I had a local version that was different than the version in agent.sh so I copied the jar I had to the agent.sh folder and updated VERSION in aaf.props
For 3:
So finally you can run
| bash agent.sh local showpass oof@oof.onap.org oof.onap |
|---|
This will prompt for oof@oof.onap.org password which is the default demo123456!
Note that if you fat finger the password you get a goofy error
org.onap.aaf.cadi.CadiException: org.onap.aaf.cadi.LocatorException: No Entries found for 'https://aaf-onap-test.osaaf.org:8095/locate/AAF_NS.cm:2.1'
which can send you on a wild goose chase.
Not sure why I bothered to obscure the passwords
Using certificates with Spring Boot Application
- Copy these 2 artifacts to a folder accessible to your application
- truststoreONAPall.jks (for outgoing HTTPS requests)
- org.onap.<app>.jks (i.e. org.onap.oof.jks) (for incoming HTTPS requests)
- Add the following to the JVM args
- -Dserver.ssl.key-store=<folder>/org.onap.oof.jks
- -Dserver.ssl.key-store-password=<cadi_keystore_password_jks>
- -Djavax.net.ssl.trustStore=<folder>/truststoreONAPall.jks







5 Comments
Matthieu Geerebaert
Hello,
Thank you very much for this tutorial
Trying to do the same for extapi, do you know login/password to use or from where we can get those credentials to access to
https://aaf-onap-test.osaaf.org:8200/gui/home
Adam Wudzinski
Hi,
try aaf_admin/demo123456!
Matthieu Geerebaert
Excellent ! Thank so much !
Matthieu Geerebaert
I am trying on windriver with aaf_admin, but even on the oof namespace I can not see any of the certificates listed in your screenshot. I am probably not doing things correctly, or understand how aaf work
harmeet kaur
Hi,
Is there any way we can logout in aaf gui.