https://www.ventx.de/blog/post/istio_oauth2_proxy/index.html
https://discuss.istio.io/t/how-to-implement-istio-authorization-using-oauth2-and-keycloak/13707
https://discuss.istio.io/t/how-to-implement-istio-authorization-based-on-keycloak-user-role/13716
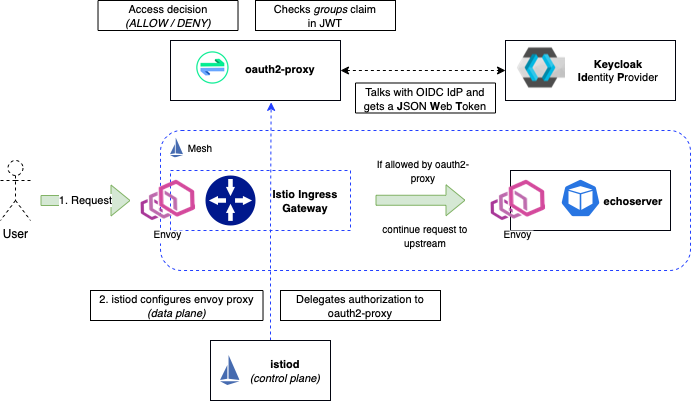
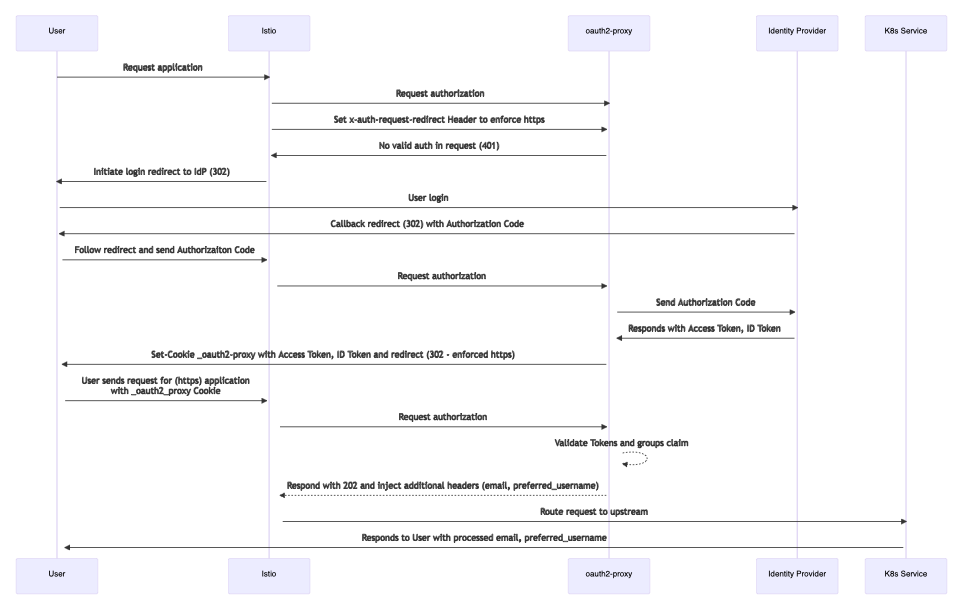
Architecture
- User requests access to an ONAP service via Istio Ingress Gateway, e.g. "https://sdc-fe-ui.simpledemo.onap.org"
- The request arrives at the Gateway, which uses the "AuthorizationPolicy" to delegate the authorization to the "external" auth component: oauth2-proxy
- "oauth2-proxy" is configured to act as client of the OICD Identity provider "Keycloak"
- If the user is not authenticated, it redirects the client to Keycloak Login page
- When the user is authenticated successfully with keycloak, the oauth2-proxy receives a JWToken including a "groups" claim for Authorization.
- oauth2-proxy evaluates the "groups" against the configured membership (e.g. "admins"). If the “admins” group is found in the JWT groups claim,
oauth2-proxy puts the Token into a Cookie and sends it back to the requesting client - our User. - The User will now be forwarded to the actual application. If the application supports it, we can configure the application to look into the headers
we inject with oauth2-proxy. This allows us to set for example the "prefered_username" or "email" attributes in the application - info we get from the ID token claims.
Configure Istiod
Add the Oauth2 proxy as ExternalAuthProvider via the Mesh-Config (see ONAP on ServiceMesh setup guide):
meshConfig:
rootNamespace: istio-config
extensionProviders:
- name: oauth2-proxy
envoyExtAuthzHttp:
service: oauth2-proxy.default.svc.cluster.local
port: 80
timeout: 1.5s
includeHeadersInCheck: ["authorization", "cookie"]
headersToUpstreamOnAllow: ["x-forwarded-access-token", "authorization", "path", "x-auth-request-user", "x-auth-request-email", "x-auth-request-access-token"]
headersToDownstreamOnDeny: ["content-type", "set-cookie"]
includeAdditionalHeadersInCheck: # Optional for oauth2-proxy to enforce https
X-Auth-Request-Redirect: 'https://%REQ(:authority)%%REQ(:path)%'
Configure Keycloak
Add Client to ONAP realm
Will be part of the REALM imported in the OOM component "platform/keycloak-init" (https://git.onap.org/oom/tree/kubernetes/platform/components/keycloak-init)
Add Client "oauth-proxy":
- Client ID: "oauth2-proxy"
- Name: "Oauth2 Proxy"
- Valid redirect URIs: "*"
Set Credentials:
- Client secret: generate and note value
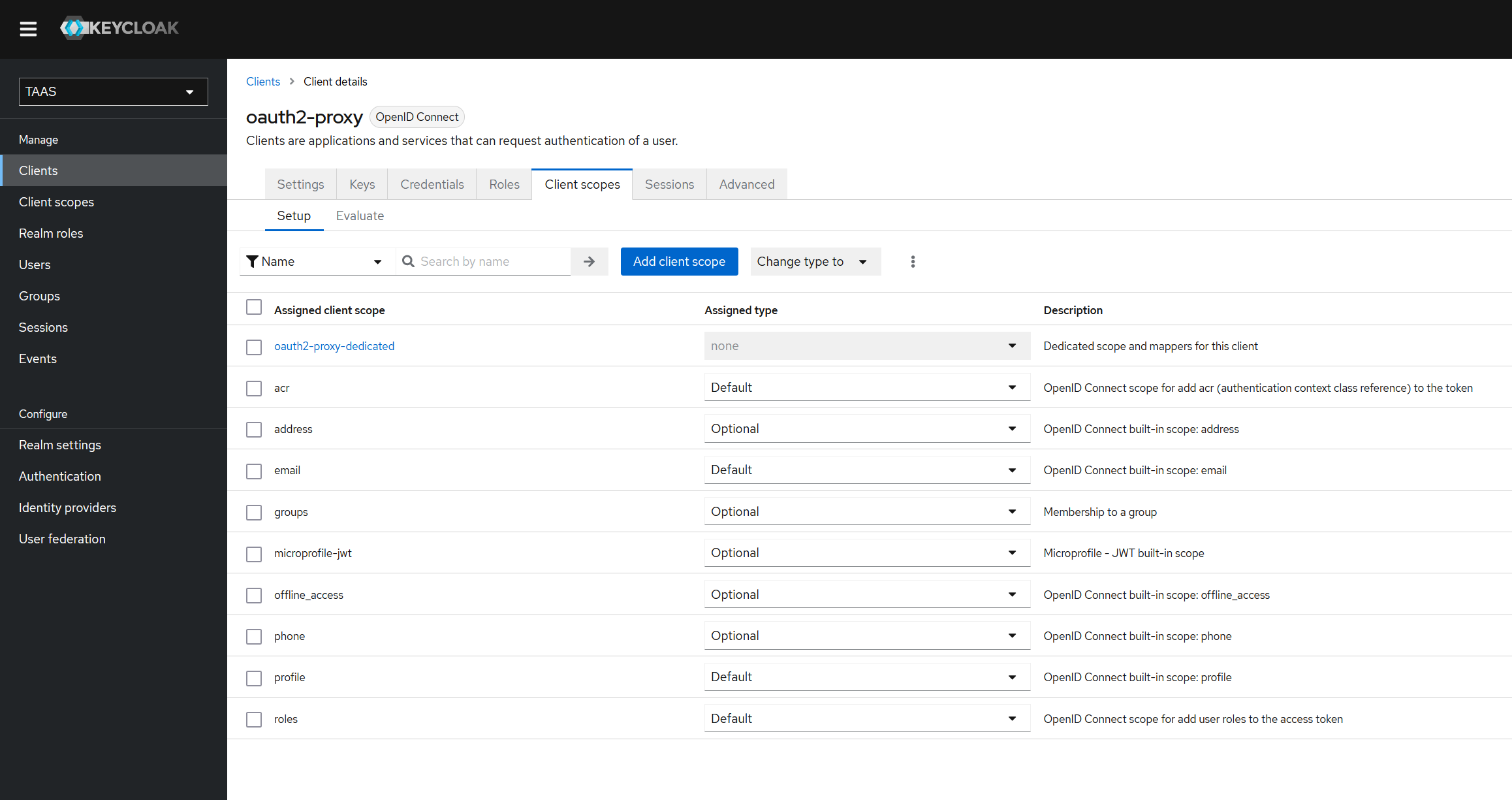
Add Client scope "groups":
with "Group Membership" mapper:
Add "groups" scope to "oatuth2-proxy" client scope:
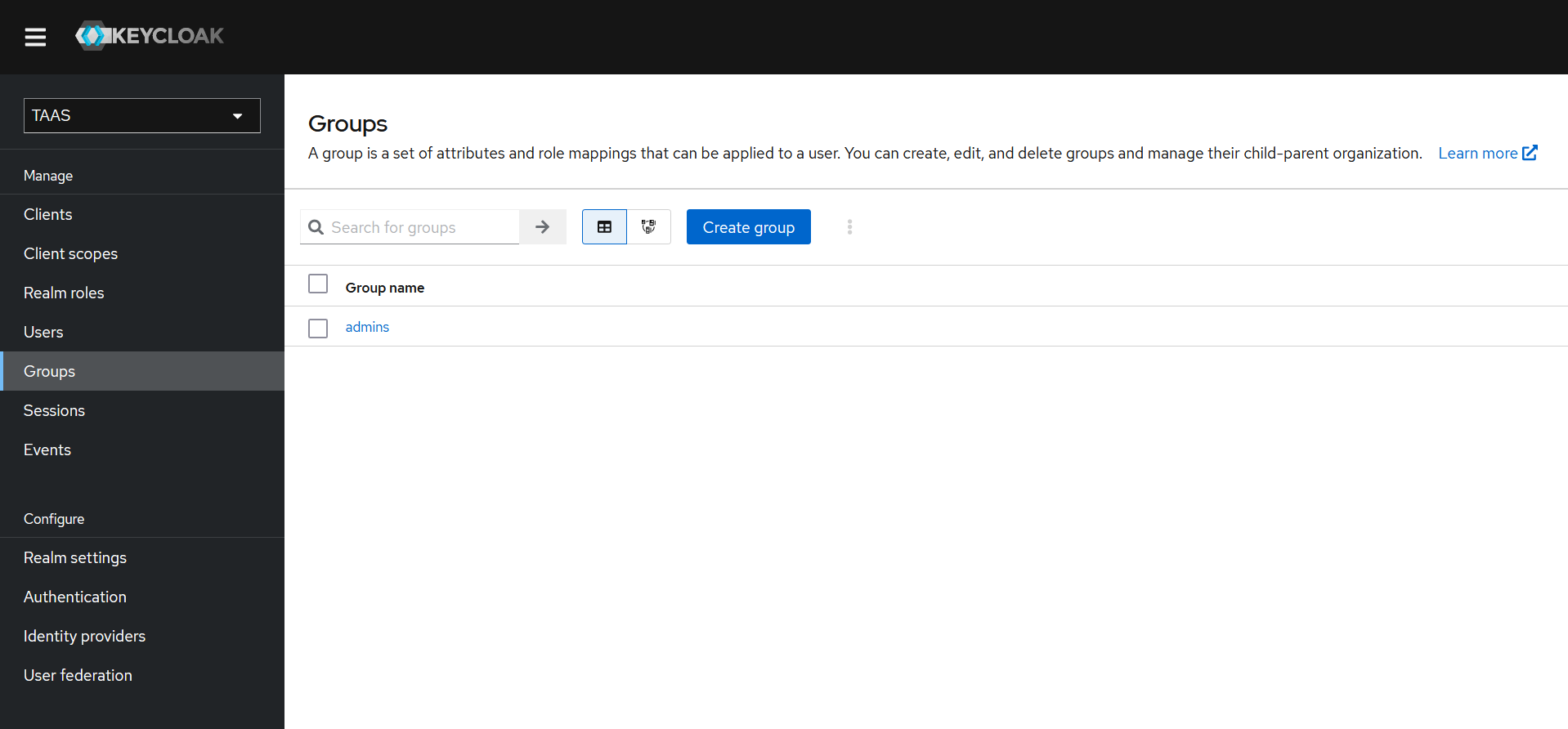
Create Group "admins" and add user to group:
Configure Oauth2-Proxy
https://oauth2-proxy.github.io/oauth2-proxy/docs/configuration/overview
The ready configured oauth2-proxy will be part of the OOM component "platform/oauth2-proxy"
Create Cookie-Secret
dd if=/dev/urandom bs=32 count=1 2>/dev/null | base64 | tr -d -- '\n' | tr -- '+/' '-_'; echo CbgXFXDJ16laaCfChtFBpKy1trNEmJZDIjaiaIMLyRA=
Configure oauth2-proxy via values.yaml using "alphaConfig"
# Oauth client configuration specifics config: cookieSecret: "CbgXFXDJ16laaCfChtFBpKy1trNEmJZDIjaiaIMLyRA=" configFile: |- email_domains = [ "*" ] # Restrict to these E-Mail Domains, a wildcard "*" allows any email alphaConfig: enabled: true configData: providers: - clientID: "oauth2-proxy" clientSecret: "5YSOkJz99WHv8enDZPknzJuGqVSerELp" id: oidc-istio provider: oidc # We use the generic 'oidc' provider loginURL: https://keycloak-ui.simpledemo.onap.org/auth/realms/TAAS/protocol/openid-connect/auth #redeemURL: https://keycloak-ui.simpledemo.onap.org/auth/realms/TAAS/protocol/openid-connect/token redeemURL: http://keycloak-http.keycloak/auth/realms/TAAS/protocol/openid-connect/token profileURL: https://keycloak-ui.simpledemo.onap.org/auth/realms/TAAS/protocol/openid-connect/userinfo validateURL: https://keycloak-ui.simpledemo.onap.org/auth/realms/TAAS/protocol/openid-connect/userinfo scope: "openid email profile groups" allowedGroups: - admins # List all groups managed at our your IdP which should be allowed access # - infrateam # - anothergroup oidcConfig: emailClaim: email # Name of the clain in JWT containing the E-Mail groupsClaim: groups # Name of the claim in JWT containing the Groups userIDClaim: email # Name of the claim in JWT containing the User ID audienceClaims: ["aud"] insecureAllowUnverifiedEmail: true insecureSkipIssuerVerification: true skipDiscovery: true # You can try using the well-knwon endpoint directly for auto discovery, here we won't use it issuerURL: https://keycloak-ui.simpledemo.onap.org/auth/realms/TAAS jwksURL: http://keycloak-http.keycloak/auth/realms/TAAS/protocol/openid-connect/certs upstreamConfig: upstreams: - id: static_200 path: / static: true staticCode: 200 # Headers that should be added to responses from the proxy injectResponseHeaders: # Send this headers in responses from oauth2-proxy - name: X-Auth-Request-Preferred-Username values: - claim: preferred_username - name: X-Auth-Request-Email values: - claim: email extraArgs: cookie-secure: "false" cookie-domain: ".simpledemo.onap.org" # Replace with your base domain cookie-samesite: lax cookie-expire: 12h # How long our Cookie is valid auth-logging: true # Enable / Disable auth logs request-logging: true # Enable / Disable request logs standard-logging: true # Enable / Disable the standart logs show-debug-on-error: true # Disable in production setups skip-provider-button: true # We only have one provider configured (Keycloak) silence-ping-logging: true # Keeps our logs clean whitelist-domain: ".simpledemo.onap.org" # Replace with your base domain
Enable AuthN+AuthZ for ONAP SDC-UI
In "London" additional configuration in the OOM values.yaml and _ingress.tpl will be done to generate the needed resource settings.
Here is the manual instruction to enable the Ingress redirection to the oauth2-proxy for SDC-FE.
- Create a "AuthorizationPolicy" for sdc-fe
---
kind: AuthorizationPolicy
apiVersion: security.istio.io/v1beta1
metadata:
name: sdc-fe-ui-authz-oauth2-proxy
namespace: istio-ingress
spec:
selector:
matchLabels:
istio: ingress
action: CUSTOM
provider:
name: oauth2-proxy
rules:
- to:
- operation:
hosts: ["sdc-fe-ui.simpledemo.onap.org"]
In case of gateway-api the solution is a bit different, as the selector is different (e.g. when a common gateway is used):
---
kind: AuthorizationPolicy
apiVersion: security.istio.io/v1beta1
metadata:
name: sdc-fe-ui-authz-oauth2-proxy
namespace: istio-ingress
spec:
selector:
matchLabels:
istio.io/gateway-name: common-gateway
action: CUSTOM
provider:
name: oauth2-proxy
rules:
- to:
- operation:
hosts: ["sdc-fe-ui.simpledemo.onap.org"]
Behaviour:
Launch SDC-FE URL :