...
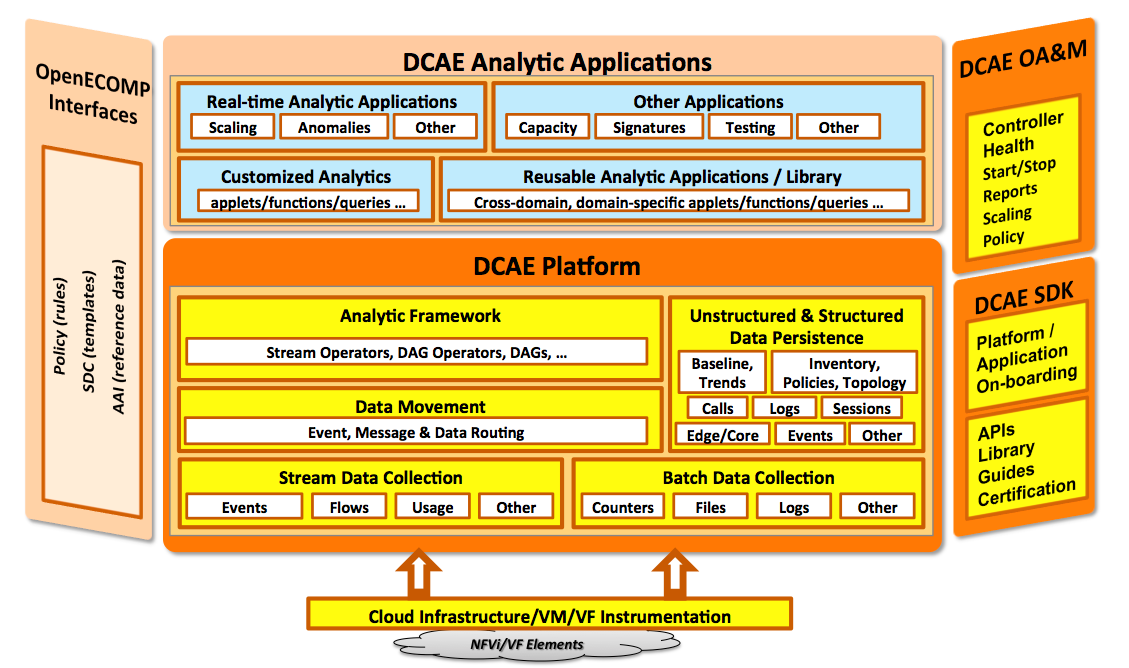
The following figure provides a functional view of the DCAE platform architecture.
DCAE Platform Components
The DCAE Platform consists of several functional components: Collection Framework, Data Movement, Storage Lakes, Analytic Framework, and Analytic Applications.
In large scale deployments, DCAE components are generally distributed in multiple sites that are organized hierarchically. For example, to provide DCAE function for a large scale OpenECOMP system that covers multiple sites spanning across a large geographical area, there will be edge DCAE sites, central DCAE sites, and so on. Edge sites are physically close to the network functions under collection, for reasons such as processing latency, data transport, and security, but often have limited computing and communications resources. On the other hand, central sites generally have more processing capacity and better connectivity to the rest of the OpenECOMP system. This hierarchical organization offers better flexibility, performance, resilience, and security.
The following figure shows the DCAE architecture:
Figure 1. DCAE Platform high-level architectureA key subset of the DCAE architecture is the DCAE Platform. The DCAE platform consists of the capabilities that help define how data is collected, moved, stored and analyzed within DCAE.
DCAE Platform Components
The DCAE Platform consists of several functional components: Common Collection Framework, Data Movement, Storage Lakes, Analytic Framework, and Analytic Applications.
In large scale deployments, DCAE components are generally distributed in multiple sites that are organized hierarchically. For example, to provide DCAE function for a large scale OpenECOMP system that covers multiple sites spanning across a large geographical area, there will be edge DCAE sites, central DCAE sites, and so on. Edge sites are physically close to the network functions under collection, for reasons such as processing latency, data transport, and security, but often have limited computing and communications resources. On the other hand, central sites generally have more processing capacity and better connectivity to the rest of the OpenECOMP system. This hierarchical organization offers better flexibility, performance, resilience, and security.
...
Collection Framework
The collection layer provides the various data collectors that are needed to collect the instrumentation that is available from the cloud infrastructure. Included are both physical and virtual elements. For example, collection of the following types of data is supported:
...
Data Movement
This component facilitates (known as DMaaP) facilitates the movement of messages and data between various publishers and interested subscribers that may reside at different sites. While a key component within DCAE, this is also the component that enables data movement between various OpenECOMP components.
...
While there may be detailed data retained at the DCAE edge layer for detailed analysis and trouble-shooting, applications should optimize the use of bandwidth and storage resources by propagating only the required data (for example, reduced, transformed, or aggregated) to the core data lake for other analyses.
...
The following list provides examples of the types of applications that can be built on top of DCAE:
...
Performance surveillance and visualization: Thisclass of application provides a window to an an operations organization, notifying them it of network and service conditions. The notifications could include outages and impacted services or customers based on various dimensions of interest. They provide visual aids ranging from geographic dashboards to virtual information model browsers to detailed drilldown to specific service or customer impacts.
...
Security: Some components of AIC the infrastructure may expose newtargets for security threats. Orchestration and control, decoupled hardware and software, and commodity hardware may be more susceptible to attack than proprietary hardware. However, SDN and virtual networks also offer an opportunity for collecting a rich set of data for security analytics applications to detect anomalies that signal a security threat, such as DDoS attack, and automatically trigger mitigating action.
...