Note: Work in Progress
Requirement
Key Contacts - @Byung-Woo Jun (Ericsson), ...
Executive Summary - Provide ASD-based CNF orchestration support through SO and its sub-components, CNFM and CNF Adapter using K8S
- Support for provisioning ASD-based CNFs using an external K8s Manager
- Instantiate and optionally overwrite the values of an application
- Terminate an application and optionally remove all relevant Persistent Volume Claims and Persistent Volumes
- Change application details using the change package function, which allows to change the deployment version of the CNF thru an upgrade or rollback (stretch goal)
- Leverage and enhance SO capabilities and adding new capabilities for ASD- and Helm-based CNF orchestration
- Orchestrator shall support the capability to use the deployment parameters from ASD for the application or CNF deployment. These deployment parameter values shall correspond to the parameters defined in the “lifecycleParameters” section(s) of the ASD.
- Orchestrator shall support the capability to construct a values file from instance specific parameter values provided at deployment time, and default values supplied in the chart.
- Orchestrator shall support the capability to perform a chart render into concrete K8S resource descriptions.
- Container resource management for determining placement for CNF application on certain K8S cluster(s), orchestrator shall support the capability to parse the workload descriptors and extract those values.
Business Impact - Enables operators and service providers to orchestrate ASD-based CNFs services along with the VNFs and PNFs
Business Markets - All operators and service providers that are intended to use the ASD-based CNFs along with PNFs / VNFs
Funding/Financial Impacts - Reduction in the footprint of the ONAP for CNF support
Organization Mgmt, Sales Strategies - There is no additional organizational management or sales strategies for this requirement outside of a service providers "normal" ONAP deployment and its attendant organizational resources from a service provider
JIRA: REQ-1043 - Getting issue details... STATUS
Concepts
- K8S CISM Cluster: Container Infrastructure Service Manager Cluster performs the same function as VIM Zone but operates on containerized application level.
- CNF: Cloud Native Network Function. Containerized VNF is designed to be deployed in the cloud as a container. CNF is a better fit for microservice architecture due to the deployment size.
- Kubernetes: Kubernetes (K8s) is an open-source system for automating deployment, scaling and management of containerized applications
- POD: A Pod is a group of one or more containers (such as Docker containers), with shared storage/network, and a specification for how to run the containers.
Scope
In Scope
See the Epic and User Stories.
Out of Scope
TBD
Epic
| Epic | Description | JIRA | priority |
|---|---|---|---|
| SO and its sub-components, CNFM, CNF Adapter, shall support ASD-based CNF lifecycle orchestration | SO and its sub-components, CNFM, CNF Adapter, shall support ASD-based CNF lifecycle orchestration (deployment and configuration) | SO-3808 - Getting issue details... STATUS | 1 |
User Story
| User Story | Affected Component | Description | JIRA | Priority | PoC Scope Y/N |
|---|---|---|---|---|---|
| SO shall get the ASD-based CNF package from SDC and store its metadata to SO Catalog DB | SDC Controller, CatalogDB Adapter, CatalogDB | SO shall get the ASD-based CNF package (SDC Service CSAR) from SDC and store its metadata to SO Catalog DB. Pre Condition:
Post Condition:
| SO-3839 - Getting issue details... STATUS | 1 | |
Task: SO SDC Controller handles ASD-based CNF Service CSAR
| 1.1 | ||||
Task: SO Catalog DB Handling for ASD-based CNF packages
| 1.2 | ||||
| For ASD-based CNF provisioning, SO shall process model info and decide flows | API Handler, RequestDB Adapter, RequestDB, SO BPMN Infra, AAI SO CNFM | For ASD-based CNF provisioning, SO shall process model info and decide flows Pre Condition:
Post Condition:
| SO-3840 - Getting issue details... STATUS | 2 | |
Task: Cloud Region(s) and Tenant(s) Creation in AAI
| 2.1 | ||||
Task: Create & Configures ASD-based CNF workflows
| 2.2 | ||||
Task: SO API Handler Enhancement
| 2.3 | ||||
Task: SO Create Service Instance to AAI
| 2.4 | ||||
Task: SO BPMN Infra processes for ASD-based VF
| 2.5 | ||||
Task: SO BPMN Infra Invocation for SO CNFM for AS LCM
| 2.6 | ||||
| SO CNFM shall process ASD-based CNF Lifecycle orchestration | SO CNFM, ASD Repository, Helm Artifact Repository, OOF, AAI, SDNC Adapter, SDNC | SO CNFM shall process ASD-based CNF Lifecycle orchestration Pre Condition:
Post Condition:
Note: in the initial PoC, ASD external CPDs parameters for the primary network will be used (e.g., loadbalancerIP, externalIPs) to configure the K8s service or ingress controller that the ExtCpd represents Note: ASD Registry, Helm Artifact Registry, Image Artifact Registry will be handled by another Epic, which is defined in Application Package Distribution | SO-3841 - Getting issue details... STATUS | 3 | |
Task: Create SO CNFM and make it available in ONAP
| 3.1 | ||||
Task: Create ASD LCM REST API Swagger
| 3.2 | ||||
Task: Support for SO CNFM NBI API Handler
Note: for the initial PoC, registration and deregistration could be out of scope (stretch goal) | 3.3 | ||||
Task: SO CNFM Input Parameter Handling
| 3.4 | ||||
Task: SO CNFM Accesses ASD Registry for Getting ASD
Note: for initial PoC, it is possible ASD is received from SDC (tbd) | 3.5 | ||||
Task: SO CNFM Processes ASD
Note: for initial PoC, Helm Charts are received from SDC (tbd) | 3.6 | ||||
Task: Create SO CNFM Instance Database Management
| 3.7 | ||||
Task: SO CNFM Processes Instance-Level Helm Charts
| 3.9 | ||||
Task: SO CNFM Transforms Enhanced Helm Charts to K8S Resource Description
| 3.10 | ||||
Task: SO CNFM Gets an AS Placement Information for a Target K8S Cluster
| 3.11 | ||||
Task: SO CNFM Makes a AS Placement Decision for a Target K8S Cluster
| 3.12 | ||||
Task: SO CNFM Supports Target K8S Clusters Registration
| 3.13 | ||||
Task: SO CNFM Supports Target K8S Clusters Deregistration
| 3.14 | ||||
Task: SO CNFM Provides a List of Registered K8S Clusters
| 3.15 | ||||
Task: SO CNFM Helm Client Process for AS Deployment
| 3.16 | ||||
Note: for the initial PoC, the SO CNF Adapter will not be used. | |||||
Task: SO CNFM Updates the AS CNF Instance to AAI
| 3.17 | ||||
SO Client shall send requests for ASD-based CNF orchestration (note: E2E support is out of PoC scope) | SO Client, SO, SO BPMN, SO CNFM | SO Client shall send requests for ASD-based CNF orchestration to SO Pre Condition:
Post Condition:
| SO-3842 - Getting issue details... STATUS | 4 | |
Task: SO Client Invokes SO for AS LCM orchestartion
| 4.1 |
Overall Process
- Pre-Conditions
- SDC accepts onboarding App packages, including ASD and DeploymentItems models, Helm Charts, Images and other artifacts, what allows to keep decomposition of Service instance
- SO subscribes and receives package notifications from SDC
- ASD-Based CNF LCM Orchestration
- Based on the notifications, SO ASDC Controller queries for the App packages from SDC, and stores models and artifacts to SO Catalog Database
- MACRO workflow in SO is used for orchestration
- ASD supports multiple Helm Charts in CNF packages.
- ASD instance will be decomposed to find its associated deployment item(s).
ASD-Based App Package Type
- The Resource VF(s) in the onboarded Service CSAR will have the following resource main manifest file
- application_name
- application_provider
- release_date_time
- entry_definition_type [ "asd"]
- SO distinguishes the App package based on the "entry_defintion_type" metadata.
- If it is "asd", SO will process the package as the ASD-based CNF.
- SO delegates the ASD-based CNF orchestration to the CNF Manager
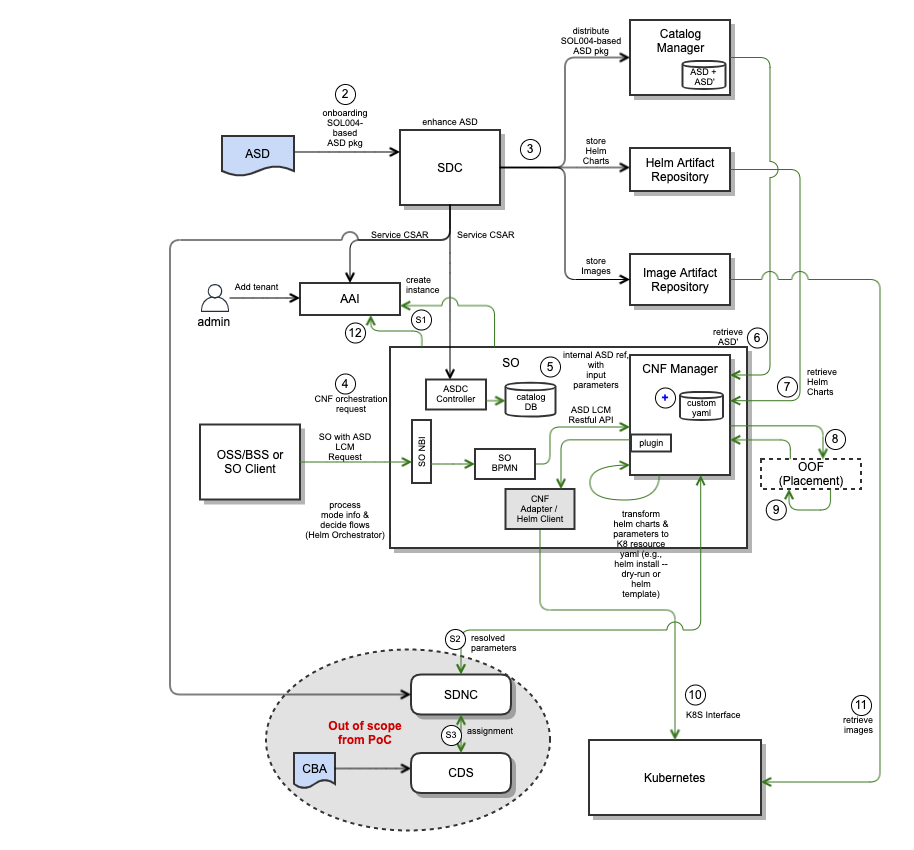
LCM Architecture Overview
The following diagram depicts LCM Architecture for the ASD-based CNF.
SO Internal Architecture
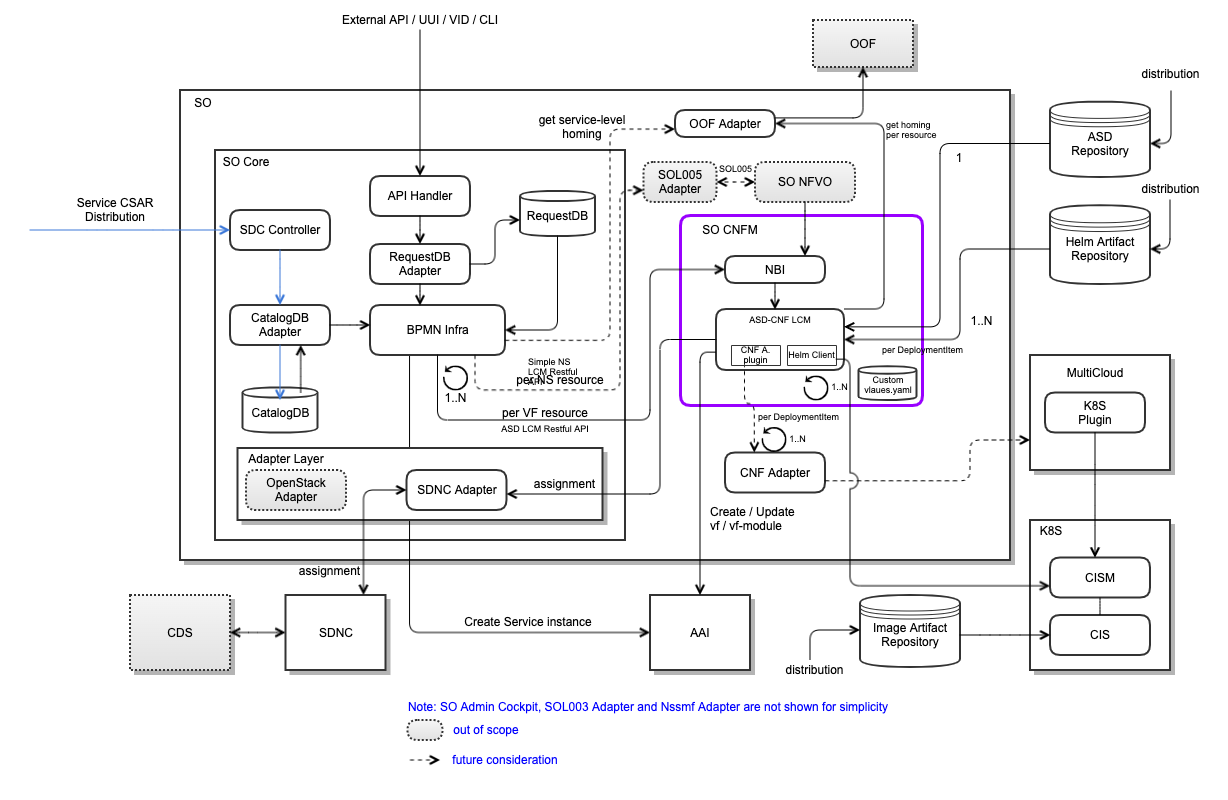
The following diagram depicts SO internal architecture for the ASD-based orchestration:
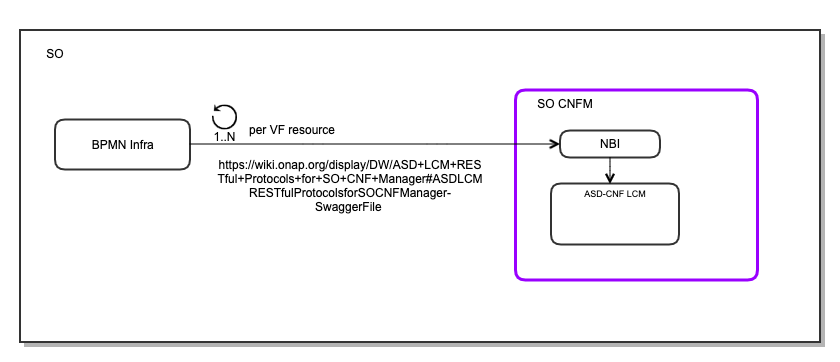
AS LCM Restful API
Please refer to the section, ASD LCM RESTful Protocols for SO CNF Manager .
- Swagger file (ASD LCM RESTful Protocols for SO CNF Manager)
ASD LCM Operations
<as_create_instantiate.bpmn example>
Process Sequence
Create and Instantiate AS
- <Preconditions>:
- Registar K8S Cluster(s) to ONAP
- During the registration, SO CNFM creates .kube/{target K8S cluster name}.config file(s)
- <SO BPMN Infra>
- BPMN Infra workflow gets VF Resource TOSCA.meta.
- In there, the entity_defintion_type is found and it is set to "asd", BPMN infra launches the AS LCM Workflow as the above.
- The workflows sends a request for Create AS Identifier to SO CNFM
- <Create an AS Identifier>
- SO CNFM receives the create request (CreateAsRequest) and processes the request and return a response with AsInstance
CreateAsRequest:
asdId
Identifier (UUID) 1 Identifier that identifies the ASD which defines the AS instance to be created. asInstanceDescription
String 0..1 Human-readable description of the AS instance to be created. asInstanceName
String 0..1 Human-readable name of the AS instance to be created. The client passes "asdId" to SO CNFM, so CNFM can query an ASD with the asdId from the ASD Repository
- SO CNFM copies the incoming CreateAsRequest attributes into an AsInstance structure, and persists the AsInstance, which has a connection between the asInstanceId and asdId
- note: SO CNFM will uses the asdId when it queries an ASD from the ASD Repository during the instantiation operation
- When the Create AS instance is successful, SO CNFM returns 200 OK with the AsInstance
- The returned AsInstance contains the asInstanceId
- Subsequent operations uses the asInstanceId; i.e., the Client use the asIstanceId in the REST Api path
- SO CNFM receives the create request (CreateAsRequest) and processes the request and return a response with AsInstance
- <Instantiate an AS>
- BPMN Infra sends an AS instantiate request to SO CNFM with the asInstanceId as follows:
- POST .../as_instances/{asInstanceId}/instantiate (InstantiateAsRequest)
- InstantiateAsRequest
Attribute Name
Data Type
Cardinality
Description
asdExtCpdInputParams
ExtCpdParams
0..N contains ext cpd parameter instance-level value deploymentItems
DeploymentItems 1..N contains lifecycle parameters for deploymentItems additionalParams KeyValuesPairs 0..1 Additional input parameters for the instantiation process (this is a pace holder to hold any additional parameters which are needed by SO CNFM)
- SO CNFM retrieves the corresponding AsInstance from its DB; it is retrieve the "asdId" for the ASD query
- SO CNFM queries an ASD with the asdId from the ASD Repository; caches the retrieved ASD in the memory during the Instantiate operations
- SO CNFM reads thru the ASD DeploymentItems, and per deploymentItems, SO CNFM queries for the associated Helm Chart (1:1) from the Helm Chart Repository
- caches the retrieved Helm Charts in the memory during the Instantiate operations
- SO CNFM reads the deploymentItems.deploymentOrder. Based on the order sequence, SO CNFM processes the deploymentItems one by one
- For each, deployment item,
- SO CNFm creates vf-modules in AAI
- SO CNFM assignes vf-modules in SDNC
- From the InstantiateAsRequest, SO CNFM retrieves the deploymentItems
DeploymentItems
deploymentItemId Identifier 1 Identifies which deploymentItem lifecycleParameterKeyValues
KeyValuesPairs 0..N provides lifecycle parameter keys and values - The lifecycleParameterKeyValues contains a list of customizable attributes (key) in the values.yaml with instance-level values
- From the associated Helm Chart, SO CNFM gets the values.yaml
- SO CNFM creates a new values.yaml, based on the retrieved values.yaml + lifecycleParameterKeyValues
- ==== SO CNFM processes the asdExtCpdInputParam ==== TBD
- SO CNFM performs "helm template " to render K8S resource template(s)
- With the rendered k8S resource template(s), SO CNFM gets a placement decision from the Placement component (e.g., OOF)
- Currently, use of OOF is out of the scope from the initial PoC
- In the initial PoC, a simplified placement function will be used
- Based on the placement decision, SO CNFM determines the target K8S cluster
- Set the Helm command environment to connect to the target K8S cluster
- set .kube/{target K8S cluster name}.config
- SO CNFM invokes "helm install" command with the corresponding Helm Chart and a new values.yaml
- SO CNFM will have a few South-Bound plugin (helm client, CNF Adapter, others)
- in the initial PoC, the helm client will be used
- If successful, SO CNFM update the corresponding vf-module in the AAI
- BPMN Infra sends an AS instantiate request to SO CNFM with the asInstanceId as follows:
- <Postconditions>:
- each POD is a Ready status. This ensures that each POD can serve requests.
- Some of the PODs will not reach the Ready status until a day 1 configuration is applied
- The PODs still need verification of containers with a specific ContainerState
AS LCM APIs
Create an AS Identifier
In order for an application (CNF) to be eligible for instantiation, a CNF identifier must be created to identify the application service as a unique instance.
An AS instance supports multiple deployment items (helm charts). So, the AS instance id could be used for helm release names as the prefix.
Query AS Instance Identifiers
To list all AS instances, make a GET request to SO CNFM.
GET .../aslcm/v1/as_instances
Query an AS instance by Instance ID
To query a specific AS instance by its instance ID, make a GET request to SO CNFM.
GET .../aslcm/v1/as_instances/{asInstanceId}
Instantiate an AS
- To instantiate an AS, make a poST request to SO CNFM. The target cluster name is included in the requrest parameter.
POST .../as_instances/{asInstanceId}/instantiate
- if some of the parameters required for instantiation are complex and cannot fit into the additionalParams section of the JSON request body (TBD).
Upgrading an AS
This operation is referred to as the changing of an AS package.
POST .../as_instances/{asInstanceId}/change_aspkg
Terminate an AS Instance
This operation terminates an AS instance.
POST .../as_instances/{asInstnaceId}/terminate (TerminateAsRequest)
Note: for PoC, GRACEFUL termination type is not supported.
Delete an AS Identifier
This operation deletes an AS Identifier.
DELETE .../as_instances/{as_instanceId}
Note: optionally, Delete an AS Identifier could clean up resources of an AS Instance, e.g., Persistent Volumes (PVs)
===========
Register K8S Clusters
This adds an ability for CNFM to register container managers like Kubernetes. that will allow to instantiate and deploy containerized CNFs.
Note: Kubernetes is advanced and commonly used CISM as of now, but in the future, adding other CISM types could be considered. for now Kubernetes is a reference implementation.
In order to make CNFM to be able to operate K8S Clusters we need introduce K8S Cluster registration, deregistration and querying features.
- As a user I want to be able to register and list CISM Cluster, which is already deployed.
- As a user I want to name the CISM Cluster and select it’s type.
- As for main information source of k8s cluster type configuration I want to use a kubectl configuration file to feed authentication information and connectivity point information.
- As a user I want to modify and transform information upon uploading (upload certificates, change or select username and credentials).
- As a user I want to be able to query all stored information for clusters both individual cluster information and filtered list by criteria(ie name, type, status, etc).
Information needed for registration
- CISM Cluster Name
- CISM Cluster type (Kubernetes)
- CISM Cluster Server URL
- Username to access API
- Option to populate connectivity details by uploading kubeconfig file
Kubeconfig contains connectivity details for the K8s cluster(hostname, port, apiRoot), which includes authentication details, too
- Certificate Authority
========
To instantiate an AS on an non-ONAP K8S cluster, a cluster configuration file that is specific to the cluster must be uploaded.
To add a cluster configuration file of a cluster, create a POST request .../aslcm/v1/clusterconfigs will be performed.
- CNFM receives the clusterconfigs info and creates a cluster configuration file (cluster name + "." + "config" to the ./kube directory.
The kubectl configuration file is used to the body of the request to define external K8S clusters.
The cluster configuration file for a particular cluster must be retrieved from the cluster administrator.
The Cluster configuration file pre-requisities are:
- It must start with an alphanumberic character
- It can only contain alpahnumberic characters, dashes (-_, or underscores (_)
- It must end with .config
Should the cluster configuration file change for any reason, e.g., CA certificate rotation on the target cluster or client key expires, then the cluster file registered in SO CNFM/AAI shall need to be updated.
The target cluster server and port must be reachable from the SO CNFM.
- to verify the connectdion to the target cluster, run the following command from the ONAP K8S cluster
- kubectl --kubeconfig ${PATH_TO_TARGET_CLUSTER_CONFIGURATION_FILE} get namespaces
Deregister K8S Clusters
To remove a cluster configruation file, create a DELETE request. .../aslcm/v1/clusterconfig/{configName}
The configName would include the K8S Cluster name as the file prefix
CNFM will remove the "configName" + "." + "config" file from the .kube directory.
The command returns the HTTP status code 204 No Content
List Registered K8S Clusters (checking if AAI can be used)
To get details about registered clusters, create a GET request .../aslcm/v1/clusterconfigs
The API returns a paginated response, but if a customized response is needed, additional parameters for page, size, sor and filtering could be applied.
Helm Command Support
The Helm library uses the Kubernetes client library to communicate with Kubernetes. Currently, the library uses REST+JSON. It stores information in Secrets located inside of Kubernetes; i.e., it does not need its own database.
- Helm Install
- Helm Uninstall
- Helm Upgrade
Component Communication Security
The component communication security will be achieved by leveraging Service Mesh. The external Helm Artifact Repository secure communication is under discussion.
Design and Distribution of ASD Service CSAR - Day 0
The following sequence diagram depicts design and distribution of ASD service CSAR, based on CNFO. This sequence could be changed.
Instantiation of ASD Service CSAR - Day 1
The following sequence diagram depicts instantiation of ASD-based CNF.
Option A: use Helm Command:
Option B: use of CNF Adapter (this is not part of initial PoC)
Note: use of CDS is TBD.
Tenant Support
The Tenant support will be realized by Kubernetes cluster, namespace, node and container. Initially, namespace can be used to restrict API access, to constrain resource usage and to restrict what containers are allowed to do.
Assumption & Requirements (from cloud.google.com)
source: https://cloud.google.com/kubernetes-engine/docs/best-practices/enterprise-multitenancy
The best practices in this guide are based on a multi-tenant use case for an enterprise environment, which has the following assumptions and requirements:
- The organization is a single company that has many tenants (two or more application/service teams) that use Kubernetes and would like to share computing and administrative resources.
- Each tenant is a single team developing a single workload.
- Other than the application/service teams, there are other teams that also utilize and manage clusters, including platform team members, cluster administrators, auditors, etc.
- The platform team owns the clusters and defines the amount of resources each tenant team can use; each tenant can request more.
- Each tenant team should be able to deploy their application through the Kubernetes API without having to communicate with the platform team.
- Each tenant should not be able to affect other tenants in the shared cluster, except via explicit design decisions like API calls, shared data sources, etc.
Access Control
TBD
Network Policies
TBD
Resource Quotas
TBD
AAI Data Model
AAI CNF Model - Overview
Note: the following overview came from the Direct CNFO AAI CNF Model. We will start it from here and will finalize the AAI model of ASD-based CNF.
- Currently no CNF Resources information is visible in ONAP AAI - agree
- Some interfaces are already implemented (Multicloud k8s Status/Query API) that
allow retrieval of detailed resources information - plan to leverage existing interfaces if they are appropriate - Initial implementation of CNF Model in AAI should be simple and allow user to
know about resources available and where to get their exact status from - plan to leverage the CNF model in AAI if they are appropriate - Long-Term solution should design appropriate CNF Resources in AAI, providing
only the most important data and relationships about them. - TBD
AAI CNF Model
Note: the following overview came from the Direct CNFO AAI CNF Model. We will start it from here and will finalize the AAI model of ASD-based CNF.
- Create additional AAI Object storing Any CNF Resource in K8s
- This new object (eg. k8sobject) should be related to generic-vnf/vf-module and cloud-region (subresource), using similar relationship matrix as vservers
- Data stored within AAI would be very generic, containing more or less only:
- Name [string; Primary Key]
- Group, Version, Kind [strings; Primary Key]
- Namespace [string; Primary Key]
- Labels [map[string]string or []string] (depending on AAI capabilities)
- Annotations [map[string]string or []string ] (depending on AAI capabilities)
- DetailsReflink [string or object]
- This field allows AAI Object consumer to specify query toward SO CNF Adapter to get full object data
Simple AAI CNF Model - Jakarta - Initial Model
Note: the following overview came from the Direct CNFO AAI CNF Model. We will start it from here and will finalize the AAI model of ASD-based CNF.
This model was drafted for reference and requires further tuning and agreement. This model needs to be discussed further at the Modeling Subcommittee
Main assumptions of this model:
- Update existing resources schema (Cloud-Region, Generic-VNF) and/or create CNF counterparts (VF-Module)
- Store Resources definitions about Controllers (eg. Deployments), Compute (Pods, Containers), Storage (PV/PVC), Network (Pod Interfaces, Services) and Configuration resources (eg. ConfigMaps, Secrets).
- Store unclassified resources like CRDs under “Uncategorized” - like object
Use of AAI Model K8S Resource Object
We are considering reuse of AAI K8S Resource Object, which was designed for CNFO.
Use of AAI Model K8S Resource Object Relations
We are considering reuse of AAI K8S Resource Object Relations (TBD)
SO ASDC Controller Handling
ASDC Controller Enhancement
SO Catalog DB Enhancement
VF-VF-Module-Helm Package
- During SDC onboarding, the ASD is mapped to VF, and the DeploymentItems is mapped to Vf-Module
- SO expects ASD VSP onboarding packages has the Native Helm, without Dummy Heat.
- VF is split into multiple vf-modules. each vf-module is dedicated to one Helm package.
- each Helm application after instantiation is visible to ONAP as a separate vf-module
Deployment Components
note: the current CNFO; will be changed for ASD-based CNF orchestration
| ONAP Component | Description |
|---|---|
| AAI | Required for Inventory Cloud Owner, Customer, Owning Entity, Service, Generic VNF, VF-Module |
| SDC | VSP, VF and Service Modeling of the ASD-based CNF |
| SO | Required for Macro Orchestration using the generic building blocks |
| CNF Adapter | |
| SDNC | Provides GENERIC-RESOURCE-API for cloud instantiation orchestration via CDS |
| Policy | used to store naming policy |
| Portal | required to access SDC |
| CDS | TBD |
| CNFM | |
| MultiCloud | TBD |
| Runtime Catalog Mgr | |
| Helm Artifact Repository | |
| Image Artifact Repository |
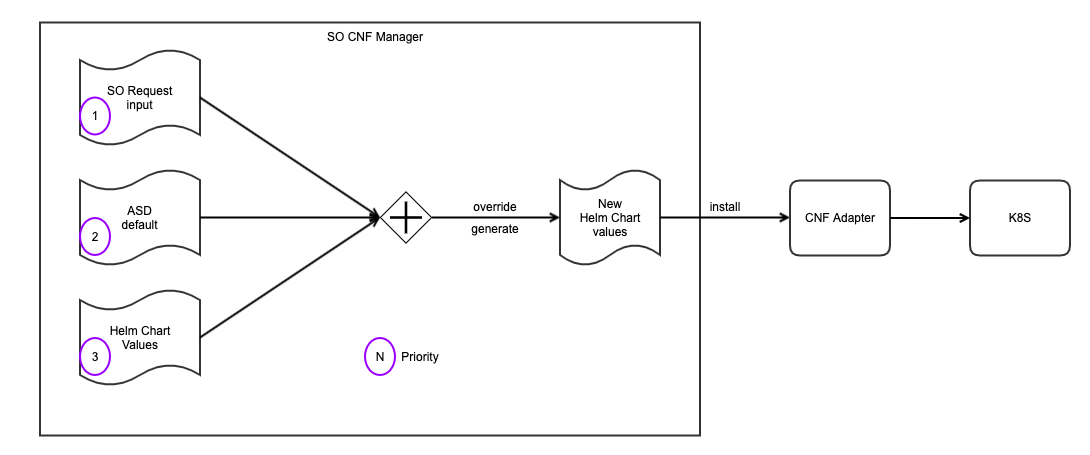
SO CNF Manager Input Parameter Handling