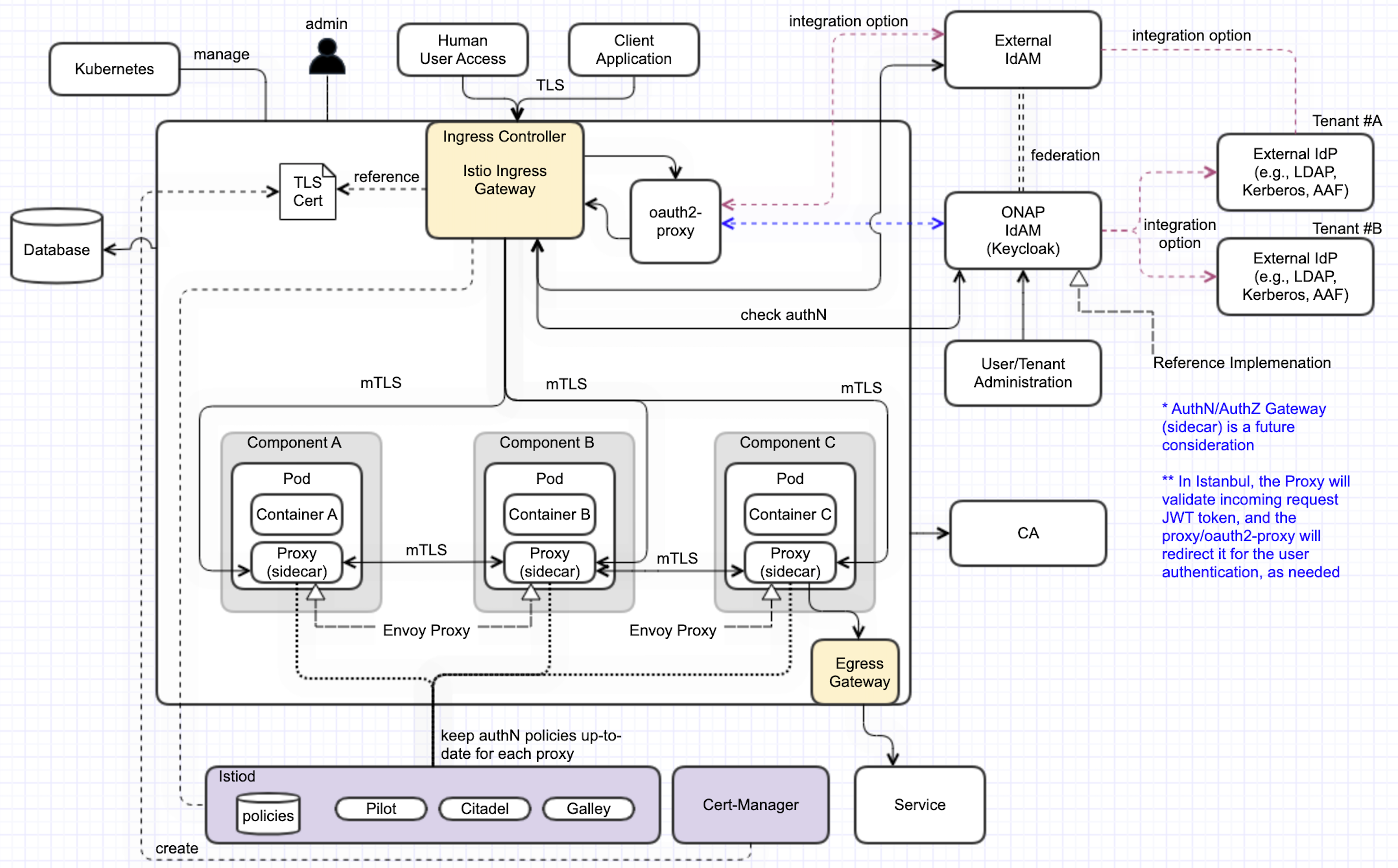
Background
After the SM PoC (Guilin) we are focussing in deploying SM in Kohn using Istio as SM framework in ONAP.
Target picture is described in SECCOM page:
ONAP Next Generation Security & Logging Architecture
Cluster Preparation
During the setup of the K8S Cluster the Istio resources need to be dinstalled.
As basis in Kohn we use the following platform versions:
- helm_release: v3.8.2
- kubernetes_release: v1.23.8
- istio_release: 1.14.1
Install Istio
Source: https://istio.io/latest/docs/setup/install/helm/
Istio basics
Configure the Helm repository:
$ helm repo add istio https://istio-release.storage.googleapis.com/charts $ helm repo update
Create a namespace istio-system for Istio components:
$ kubectl create namespace istio-system
Install the Istio Base chart which contains cluster-wide resources used by the Istio control plane:
$ helm upgrade istio-base istio/base -n istio-system --version 1.14.1
Install the Istio Discovery chart which deploys the istiod service:
(enable the variable to enforce the (sidecar) proxy startup before the container start)$ helm upgrade istiod istio/istiod -n istio-system --version 1.14.1 --wait --set global.proxy.holdApplicationUntilProxyStarts=true
Istio Ingress Gateway
Create a namespace istio-ingress for the Istio Ingress gateway and enable istio-injection:
$ kubectl create namespace istio-ingress $ kubectl label namespace istio-ingress istio-injection=enabled
Install the Istio Gateway chart:
$ helm upgrade istio-ingress istio/gateway -n istio-ingress --version 1.14.1 --wait
Install Jaeger/Kiali
Configure ONAP charts
Global settings
Global values used for ServiceMesh and Ingress setup can be found in
- https://git.onap.org/oom/tree/kubernetes/onap/values.yaml
- https://git.onap.org/oom/tree/kubernetes/onap/resources/overrides/onap-all-ingress-istio.yaml
The following variable settings are used for enabling ServiceMesh as well as Istio Ingress:
#ingress virtualhost based configuration
global:
ingress:
enabled: true
virtualhost:
baseurl: "simpledemo.onap.org"
# All http requests via ingress will be redirected
config:
ssl: "redirect"
# you can set an own Secret containing a certificate
# tls:
# secret: 'my-ingress-cert'
# optional: Namespace of the Istio IngressGateway
namespace: istio-ingress
...
serviceMesh:
enabled: true
tls: true
# be aware that linkerd is not well tested
engine: "istio" # valid value: istio or linkerd
aafEnabled: false
cmpv2Enabled: false
tlsEnabled: false
msbEnabled: false
ServiceMesh settings:
- enabled: true → enables ServiceMesh functionality in the ONAP Namespace (Istio: enables Sidecar deployment)
- tls: true → enables mTLS encryption in Sidecar communication
- engine: istio → sets the SM engine (currently only Istio is supported)
- aafEnabled: false → disables AAF usage for TLS interfaces
- tlsEnabled: false → disables creation of TLS in component services
- cmpv2Enabled: false → disable cmpv2 feature
- msbEnabled: false → MSB is not used in Istio setup (Open, if all components are MSB independend)
Ingress settings:
- enabled: true → enables Ingress using: Nginx (when SM disabled), Istio IngressGateway (when SM enabled)
- virtualhost.baseurl: "simpledemo.onap.org" → sets globally the URL for all Interfaces set by the components, resulting in e.g. "aai-api.simpledemo.onap.org"
- config.ssl: redirect → sets in the Ingress globally the redirection of all Interfaces from http (port 80) to https (port 443)
- config.tls.secret: "..." → (optional) overrides the default selfsigned SSL certificate with a certificate stored in the specified secret
- namespace: istio-ingress → (optional) overrides the namespace of the ingress gateway which is used for the created SSL certificate
Install ONAP
Label namespace for Istio sidecar injection:
$ kubectl label namespace onap istio-injection=enabled --overwrite=true